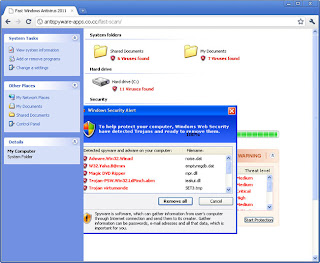
The adware blames pretty harmless programs, especially security related tools. That is the way it scans computer system.
It should be noted that, unlike most of other programs of its tribe, the adware actually scans computer system. However, instead of viruses, it looks for programs which are quite legitimate.
First of all, it targets computer security tools as they will sooner or later receive Win 7 Anti-Spyware 2011 removal related update, if they are genuine. That seems to be a reasonable tactic as the adware aim is to stay on a computer system as long as possible.
Second place in the queue of programs detected by adware is reserved for the most frequently used software. The objective of that is less evident, but is quite clear after a bit of consideration. It is to lure users into deleting essentials of software they use most frequantely.
The adware usually provides location details for entries it proclaims to be threats so that users are tempted to make havoc with their own hands. In the meantime, the adware is not idle and itself deletes security tools, where it is possible, for even poor but original security tools are usually protected from the adware aggression, and other programs which it finds necessary to destroy.
With such a security postponing Win 7 Anti-Spyware 2011 is not a reasonable thing to do. Click here to download and install free scanner in shortest terms to get rid of Win 7 Anti-Spyware 2011 as one of the threats found.
It should be noted that, unlike most of other programs of its tribe, the adware actually scans computer system. However, instead of viruses, it looks for programs which are quite legitimate.
First of all, it targets computer security tools as they will sooner or later receive Win 7 Anti-Spyware 2011 removal related update, if they are genuine. That seems to be a reasonable tactic as the adware aim is to stay on a computer system as long as possible.
Second place in the queue of programs detected by adware is reserved for the most frequently used software. The objective of that is less evident, but is quite clear after a bit of consideration. It is to lure users into deleting essentials of software they use most frequantely.
The adware usually provides location details for entries it proclaims to be threats so that users are tempted to make havoc with their own hands. In the meantime, the adware is not idle and itself deletes security tools, where it is possible, for even poor but original security tools are usually protected from the adware aggression, and other programs which it finds necessary to destroy.
With such a security postponing Win 7 Anti-Spyware 2011 is not a reasonable thing to do. Click here to download and install free scanner in shortest terms to get rid of Win 7 Anti-Spyware 2011 as one of the threats found.
Win 7 Anti-Spyware 2011 GUI snapshot:
Win 7 Anti-Spyware 2011 remover:
Win 7 Anti-Spyware 2011 manual removal:
Delete infected files:
%Documents and Settings%\All Users\Application Data\[random]\
%Documents and Settings%\All Users\Application Data\[random]\[random].exe
%Documents and Settings%\All Users\Application Data\[random]\[random].mof
%Documents and Settings%\All Users\Application Data\[random]\[random].dll
%Documents and Settings%\All Users\Application Data\[random]\[random].ocx
%Documents and Settings%\All Users\Application Data\[random]\[random]\
%UserProfile%\Application Data\Best Malware Protection\
%UserProfile%\Application Data\Best Malware Protection\cookies.sqlite
%UserProfile%\Application Data\Best Malware Protection\Instructions.ini
Delete infected registry entries:
HKEY_CLASSES_ROOT\PersonalSS.DocHostUIHandler
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Download “RunInvalidSignatures” = “1″
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “ProxyServer” = “http=127.0.0.1″
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “PC Security Guardian″
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options “Debugger” = “svchost.exe”